top of page


Valuing Secrets: Personal Details
Even if they do not have a data-mining strategy, most businesses have some personal customer data, and it can be valuable to thieves
4 min read


Valuing Secrets: Medical Information
Medical records do get stolen. While we cannot say for certain, it seems that there is little criminal interest in buying them.
4 min read


Valuing Secrets - Login Information
One of the workhorses of modern internet crime is something boring and simple: a username and password.
4 min read


Handling Data: Credit Cards
Do you store and process credit cards from customers?
The credit card companies wish you wouldn’t.
5 min read


Valuing Secrets: Proprietary Client Information
This article is part of the Handling Secrets series. In this first part, Valuing Secrets, we describe how to rate the likelihood of theft...
2 min read


Valuing Secrets
This article is part of the Handling Secrets series. In this first part, Valuing Secrets, we describe how to rate the likelihood of theft...
5 min read

Handling Secrets
Part of our series on Handling Secrets. Do you have secrets? I have asked this question hundreds of times. Most say no. You do. Your most...
3 min read


Stopping Fraud: Register with D&B
Part of our series on Security for Medium Businesses. Did you know that your business has a profile and credit history? Just like your...
3 min read


Stopping Fraud: For the Low-Tech Business
Part of our series on Security for Medium Businesses. “Bah,” you say. “None of this newfangled fraud applies to me because I do not use...
3 min read


Stopping Fraud: Messaging
Part of our series on Security for Medium Businesses. Note: while understanding is not wholly predicated on formal accreditation, Simple...
4 min read


Stopping Fraud: Contracts
Part of our series on Security for Medium Businesses. Note: while understanding is not wholly predicated on formal accreditation, Simple...
4 min read


Stopping Fraud: Three Way Match
Part of our series on Security for Medium Businesses. Last week, we discussed how maintaining a list of Valid Vendors can help prevent...
3 min read


Stopping Fraud: Vendor Governance
Part of our series on Security for Medium Businesses. Cheating is older than history. The oldest intact written record is a complaint...
3 min read


Stopping Fraud: Eliminating Email Forgery
Part of our series on Security for Medium Businesses. I’ll be straight with you: today’s article strays into tech. Today’s...
4 min read


Stopping Fraud: Payment Interception
Part of our series on Security for Medium Businesses. Basics of the Scam One of the most common sources of successful business fraud is...
4 min read


Stopping Fraud
Part of our series on Security for Medium Businesses. As we’ve covered extensively, the biggest security threat to organizations is...
2 min read

Least Privilege 4: Access Governance
Part of our series on Security for Medium Businesses. So there’s a joke that metrics nerds love to tell, especially those in security. A...
5 min read


Least Privilege 3: Roles and Segregation of Duties
Last time we discussed how to drive Least Privilege by automatically expiring access and by eliminating generic accounts. To this point,...
5 min read
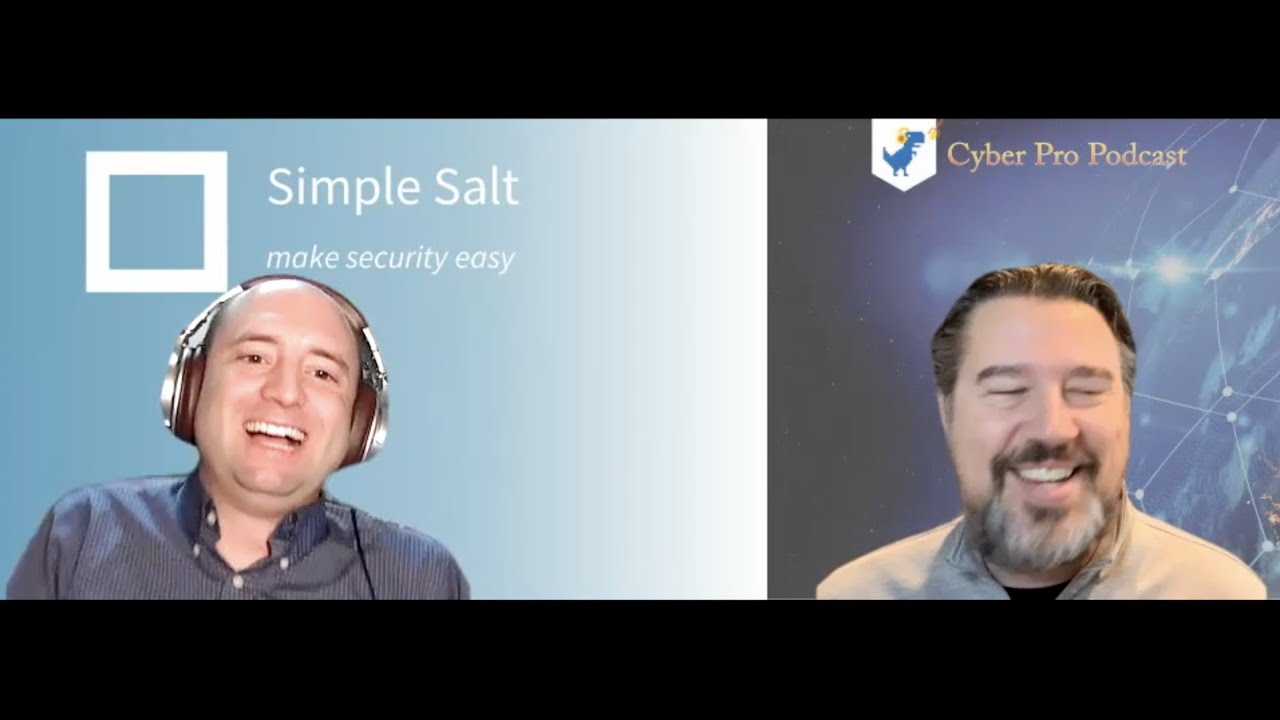

Guest Appearance on Cyber Pro Podcast
Watch Dylan get interviewed on the Cyber Pro Podcast with Rick Mischka. Platform-specific links: LinkedIn PodBean Apple Podcast Spotify...
1 min read


Secure Fileshares the Easy Way
Fileshares can be a huge security risk. They are vulnerable to ransomware and theft of secrets. If you collaborate with customers, you...
1 min read
Learn More
Read articles and watch guides on improving your organization's resistance to internet crime.
Looking for something specific? search for it here:
bottom of page